The security and vulnerability management market is experiencing robust growth driven by escalating cyber threats, stringent regulatory frameworks, and increasing digital transformation initiatives across industries. Organizations are prioritizing proactive risk mitigation and compliance adherence, which is elevating demand for advanced security solutions. The current landscape is shaped by the rapid adoption of cloud platforms, hybrid IT infrastructures, and remote working models that have expanded the threat surface.
Vendors are investing in automation, artificial intelligence, and machine learning to improve real-time threat detection and response efficiency. The future outlook indicates steady expansion as enterprises strengthen their cybersecurity postures and adopt integrated vulnerability management frameworks.
Growth rationale is centered on the increasing necessity for continuous monitoring, the integration of predictive analytics for threat prevention, and the emphasis on end-to-end visibility of network vulnerabilities These factors are collectively positioning the market for consistent revenue growth, broader enterprise adoption, and long-term operational resilience.
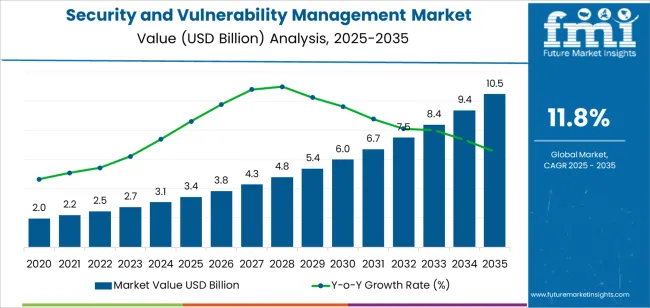
| Metric | Value |
|---|---|
| Security and Vulnerability Management Market Estimated Value in (2025 E) | USD 3.4 billion |
| Security and Vulnerability Management Market Forecast Value in (2035 F) | USD 10.5 billion |
| Forecast CAGR (2025 to 2035) | 11.8% |
The market is segmented by Component, Enterprise Type, and Vertical and region. By Component, the market is divided into Software and Services. In terms of Enterprise Type, the market is classified into Large Enterprises, Small Enterprises, and Medium Enterprises. Based on Vertical, the market is segmented into BFSI, IT And Telecom, Retail, Government, Healthcare, Utility, Defence, and Others. Regionally, the market is classified into North America, Latin America, Western Europe, Eastern Europe, Balkan & Baltic Countries, Russia & Belarus, Central Asia, East Asia, South Asia & Pacific, and the Middle East & Africa.
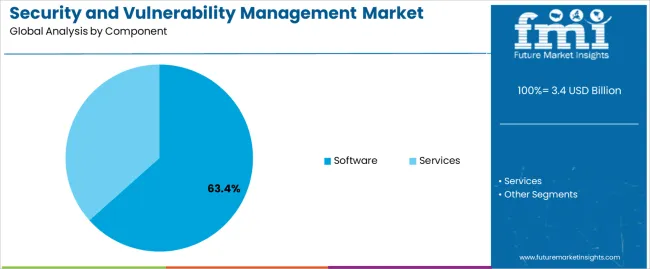
The software segment, accounting for 63.40% of the component category, has emerged as the dominant contributor owing to its critical role in automating threat detection and risk assessment processes. Organizations are adopting software-driven solutions to ensure scalable, real-time vulnerability scanning and prioritization.
The segment’s growth is being reinforced by continuous product innovations, integration of AI-based analytics, and enhanced reporting capabilities that support compliance management. Increased deployment across hybrid and multi-cloud environments has further strengthened market penetration.
The adaptability of software platforms to integrate with existing IT ecosystems and security tools is ensuring seamless operations As enterprises continue to modernize their digital infrastructure, the demand for centralized, automated, and intelligent vulnerability management software is expected to remain strong, sustaining the segment’s leadership position over the forecast period.
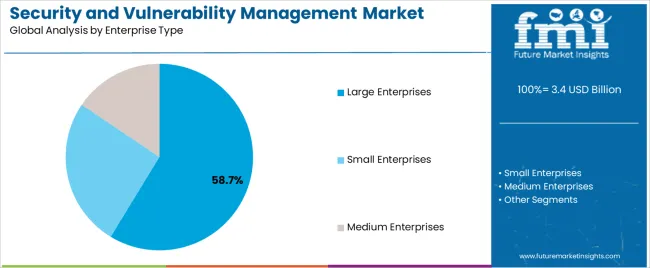
The large enterprises segment, representing 58.70% of the enterprise type category, is leading the market due to higher exposure to complex cyber risks and greater resource allocation toward comprehensive security frameworks. These organizations are emphasizing enterprise-wide vulnerability assessments, patch management, and compliance auditing to safeguard critical assets.
Strategic investments in dedicated cybersecurity teams and partnerships with managed security service providers have reinforced resilience against evolving threats. The segment’s dominance is supported by extensive IT infrastructure, data-driven operations, and regulatory obligations that necessitate continuous monitoring and incident response readiness.
Ongoing digital transformation initiatives, coupled with the adoption of zero-trust architectures and advanced analytics, are expected to sustain market share and further strengthen security capabilities among large-scale enterprises globally.
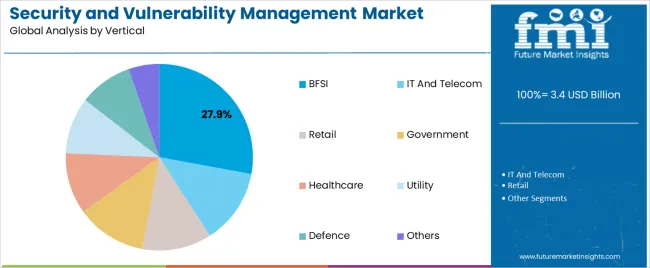
The BFSI segment, holding 27.90% of the vertical category, has maintained its leading position owing to the sector’s high susceptibility to data breaches, financial fraud, and regulatory scrutiny. Financial institutions are deploying robust vulnerability management frameworks to ensure real-time threat detection, compliance with data protection mandates, and secure transaction environments.
Growth within this segment is being driven by increasing reliance on digital banking, fintech expansion, and cloud-based service adoption. The integration of advanced analytics and continuous monitoring tools has improved response times and risk prioritization.
Additionally, strategic collaborations with cybersecurity vendors and regulatory compliance initiatives are reinforcing sectoral security resilience As financial ecosystems continue to evolve, the BFSI sector is expected to remain a key adopter of security and vulnerability management solutions, underpinning sustained revenue contribution to the overall market.
| Attributes | Details |
|---|---|
| Market Value for 2020 | USD 1934.2 million |
| Market Value for 2025 | USD 2786.9 million |
| Market CAGR from 2020 to 2025 | 9.6% |
The segmented security and vulnerability management market analysis included in the following subsection. Based on comprehensive studies, the security and vulnerability management software sector are leading the component category, and the security and vulnerability management for large enterprises segment is commanding the enterprise type category.
| Segment | Security and Vulnerability Management Software |
|---|---|
| Share (2025) | 74.2% |
| Segment | Security and Vulnerability Management for Large Enterprises |
|---|---|
| Share (2025) | 40.6% |
The security and vulnerability management market can be observed in the subsequent tables, which focus on the leading economies in the Germany, Japan, China, the United States, and Australia. A comprehensive evaluation demonstrates that Australia has enormous market opportunities of security and vulnerability management.
| Country | Australia |
|---|---|
| CAGR (2025 to 2035) | 15.3% |
| Nation | China |
|---|---|
| CAGR (2025 to 2035) | 12.3% |
| Nation | United States |
|---|---|
| CAGR (2025 to 2035) | 8.6% |
| Nation | Germany |
|---|---|
| CAGR (2025 to 2035) | 7.2% |
| Nation | Japan |
|---|---|
| CAGR (2025 to 2035) | 6.5% |
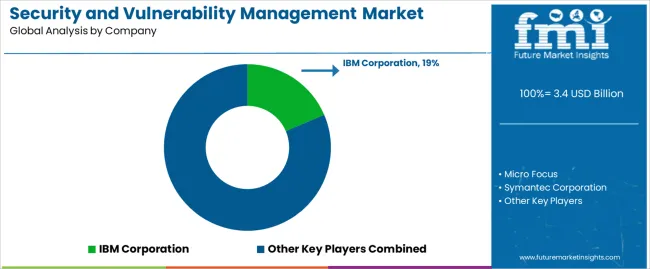
The market has fierce competition, with major security and vulnerability management vendors vying for supremacy. Leaders in the field include well-known security and vulnerability management providers like Symantec Corporation, IBM Corporation, and Micro Focus, all of whom use their knowledge to offer strong security solutions. Rapid7 Inc. and Qualys Inc. always innovate to tackle new threats and weaknesses.
On the other hand, Tenable Inc. and Trend Micro Inc. support a broad spectrum of businesses and use cases with their all-inclusive security services, which support the security and vulnerability management industry.
McAfee LLC and Tripwire Inc. diversify the security incident and event management market by bringing their distinct advantages to the table. RSA Security LLC (Dell EMC) is a major player that pools its resources and expertise to provide innovative security solutions.
These major cybersecurity risk management providers invest in ongoing innovation and strategic collaborations as the competition heats up to maintain their lead in the quickly changing security field.
Their differentiation in the vulnerability assessment tools market emerges from their customer-centric approaches and emphasis on delivering value-added services.
These security information and event management (SIEM) suppliers continue to play a critical role in protecting enterprises against emerging threats, influencing the direction of security and vulnerability management in light of the growing significance of cybersecurity.
Noteworthy Advancements
| Company | Details |
|---|---|
| BackBox Software Inc. | BackBox Software Inc. introduced the Network Vulnerability Manager service in October 2025 to improve network automation. This new service provides an all-inclusive approach to managing vulnerabilities inside network infrastructures and helps users with network automation. |
| Hackuity | Hackuity released version 2.0 of their intelligent risk-based vulnerability management software in October 2025. The next-generation platform, version 2.0, offers significant improvements to help firms manage risks. The updated version gives companies a quantifiable True Risk Score (TRS) by fusing threat intelligence, vulnerability severity, and distinct business context. |
| Google LLC | Google LLC started the Hacking Policy Council program in April 2025 to improve vulnerability management. Intel, Bugcrowd, Intigriti, HackerOne, and Luta Security are working with the Hacking Policy Council to improve vulnerability management procedures. |
| Honeywell | In November 2025, Honeywell announced that its new operational technology (OT) cybersecurity solutions are now available to assist clients in safeguarding the reliability, availability, and safety of their industrial control systems and operations. The tools, which come with a new Advanced Monitoring and Incident Response (AMIR) dashboard and an enhanced Cyber App Control dashboard, are designed to provide businesses with round-the-clock intelligent threat detection across the expanding attack surface of their industrial control systems (ICS). |
| Israeli government | The Israeli government stated in February 2025 that it would join the American Development Bank and provide USD 2 million to this region's cybersecurity skills to launch a new cybersecurity project in the Caribbean and Latin America. |
The global security and vulnerability management market is estimated to be valued at USD 3.4 billion in 2025.
The market size for the security and vulnerability management market is projected to reach USD 10.5 billion by 2035.
The security and vulnerability management market is expected to grow at a 11.8% CAGR between 2025 and 2035.
The key product types in security and vulnerability management market are software and services.
In terms of enterprise type, large enterprises segment to command 58.7% share in the security and vulnerability management market in 2025.
Our Research Products

The "Full Research Suite" delivers actionable market intel, deep dives on markets or technologies, so clients act faster, cut risk, and unlock growth.
The Leaderboard benchmarks and ranks top vendors, classifying them as Established Leaders, Leading Challengers, or Disruptors & Challengers.

Locates where complements amplify value and substitutes erode it, forecasting net impact by horizon

We deliver granular, decision-grade intel: market sizing, 5-year forecasts, pricing, adoption, usage, revenue, and operational KPIs—plus competitor tracking, regulation, and value chains—across 60 countries broadly.

Spot the shifts before they hit your P&L. We track inflection points, adoption curves, pricing moves, and ecosystem plays to show where demand is heading, why it is changing, and what to do next across high-growth markets and disruptive tech

Real-time reads of user behavior. We track shifting priorities, perceptions of today’s and next-gen services, and provider experience, then pace how fast tech moves from trial to adoption, blending buyer, consumer, and channel inputs with social signals (#WhySwitch, #UX).
Partner with our analyst team to build a custom report designed around your business priorities. From analysing market trends to assessing competitors or crafting bespoke datasets, we tailor insights to your needs.
Supplier Intelligence
Discovery & Profiling
Capacity & Footprint
Performance & Risk
Compliance & Governance
Commercial Readiness
Who Supplies Whom
Scorecards & Shortlists
Playbooks & Docs
Category Intelligence
Definition & Scope
Demand & Use Cases
Cost Drivers
Market Structure
Supply Chain Map
Trade & Policy
Operating Norms
Deliverables
Buyer Intelligence
Account Basics
Spend & Scope
Procurement Model
Vendor Requirements
Terms & Policies
Entry Strategy
Pain Points & Triggers
Outputs
Pricing Analysis
Benchmarks
Trends
Should-Cost
Indexation
Landed Cost
Commercial Terms
Deliverables
Brand Analysis
Positioning & Value Prop
Share & Presence
Customer Evidence
Go-to-Market
Digital & Reputation
Compliance & Trust
KPIs & Gaps
Outputs
Full Research Suite comprises of:
Market outlook & trends analysis
Interviews & case studies
Strategic recommendations
Vendor profiles & capabilities analysis
5-year forecasts
8 regions and 60+ country-level data splits
Market segment data splits
12 months of continuous data updates
DELIVERED AS:
PDF EXCEL ONLINE
Seaport Security Management Market Size and Share Forecast Outlook 2025 to 2035
Data Security Posture Management (DSPM) Solutions Market Size and Share Forecast Outlook 2025 to 2035
Security Information and Event Management Software Market
Network Security Policy Management Market Size and Share Forecast Outlook 2025 to 2035
Mobile Threat Management Security Software Market Size and Share Forecast Outlook 2025 to 2035
Physical Security Information Management (PSIM) Market Size and Share Forecast Outlook 2025 to 2035
Security Tape Market Size and Share Forecast Outlook 2025 to 2035
Security Alarm Communicator Market Size and Share Forecast Outlook 2025 to 2035
Security Holograms Market Size and Share Forecast Outlook 2025 to 2035
Security Paper Market Size and Share Forecast Outlook 2025 to 2035
Security System Tester Market Size and Share Forecast Outlook 2025 to 2035
Security Advisory Services Market Size and Share Forecast Outlook 2025 to 2035
Security Room Control Market Size and Share Forecast Outlook 2025 to 2035
Security Cameras (IR Illuminator) Market Size and Share Forecast Outlook 2025 to 2035
Security Operation Centre as a Service Market Size and Share Forecast Outlook 2025 to 2035
Security Robots Market Size and Share Forecast Outlook 2025 to 2035
Security Service Edge Market Size and Share Forecast Outlook 2025 to 2035
Security and Surveillance Equipment Market Size and Share Forecast Outlook 2025 to 2035
Security Orchestration Automation and Response (SOAR) Market Size and Share Forecast Outlook 2025 to 2035
Security Bags Market Size and Share Forecast Outlook 2025 to 2035
Thank you!
You will receive an email from our Business Development Manager. Please be sure to check your SPAM/JUNK folder too.
Chat With
MaRIA