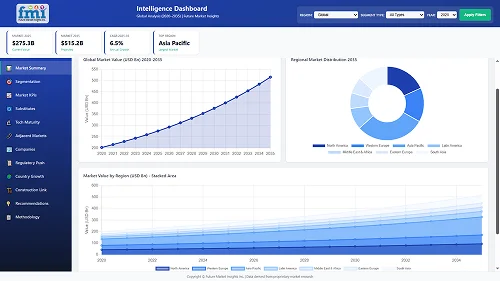
The cryptojacking solution market is estimated to be worth USD 22.1 billion in 2025 and anticipated to reach a value of USD 100.3 billion by 2035. Sales are projected to rise at a CAGR of 16.3% over the forecast period between 2025 and 2035.
The industry is in the midst of a rapid expansion due to the crime of cryptocurrency hijacking; the most frequent case of unauthorized cryptocurrency mining attacks. The industry is capturing the surge in the need for power-packed security tools, which helps not only in identifying the attacks but also in eradicating them.
The industry growth is mainly due to the increased use of cryptocurrency and blockchain technology. Consequently, the progress of digital currency transactions is inevitable and therefore, cybercriminals use advanced malware and browser-based mining scripts to hijack computing power.
Companies of different types, which are in the sectors of banking, IT, healthcare, and government, have all started to use the cryptojacking detection and prevention software to guarantee their infrastructure and networks' safety.
The rise of the cloud computing industry and the number of IoT-connected devices is also a reason why the company is growing. More and more criminals are breaking into cloud servers, mobile devices, and enterprise networks for an extensive range of cryptojacking applications.
Mostly, this gave positive feedback regarding the demand for AI threat intelligence, endpoint security tools, and behavior-based anomaly detection systems that can identify and neutralize cryptojacking threats in real time. The incorporation of security automation, zero-trust architecture, and AI-driven network traffic monitoring is, in turn, the companies further capacity to preemptively guard against unauthorized cryptocurrency mining attacks.
However, the industry has its fair share of challenges such as lack of understanding and insufficient publicity on the threats of cryptojacking, the dynamic evotion of cryptojacking malware, and inadequate regulatory frameworks for cryptocurrencies shared cybercrimes. The other issue is that some organizations with power-less cybersecurity structure might have difficulty employing good implementations of cryptojacking prevention.
These problems notwithstanding, the industry expansion potential can hardly be overemphasized. The enterprise cybersecurity resilience, which is getting more respect and the increasing spending on AI-driven threat intelligence solutions, have crossed the border with new growth possibilities.
Furthermore, the government rules and the industry partnership in curtailing the cyber threats pointing at the cryptocurrencies are expected to be the instruments driving the further innovations. The global industry for cryptojacking solutions is expected to have long-term growth for the coming years as the instances of digital threats continue to fluctuate.
Market Metrics
| Metrics | Values |
|---|---|
| Industry Size (2025E) | USD 22.1 billion |
| Industry Value (2035F) | USD 100.3 billion |
| CAGR (2025 to 2035) | 16.3% |
The industry is growing substantially, owing to the factors such as increased number of cybersecurity threats that target computing power for illicit cryptocurrency mining. Enterprises and cloud providers are the biggest adopters since cryptojacking attacks target cloud infrastructure, enterprise servers, and IoT devices, resulting in rising operation costs and system performance degradation.
Government and defense sectors are also investing in cryptojacking defense solutions to safeguard national security networks from stealthy mining malware. SMEs have less awareness and smaller budgets, typically keeping general cybersecurity over specialized cryptojacking protections.
Growing traction with AI-based threat detection, behavior analytics, and cloud-born security solutions is characterizing the industry. More and more organizations call for real-time visibility, auto-remediation for threats, and compliance-enabled products in order to resist changing cryptojacking attacks. As more regulation pushes harder toward robuster cybersecurity frameworks, deployment of leading-edge cryptojacking solutions should continue on upwards trend.
| Company | Contract/Release Details |
|---|---|
| SentinelOne | SentinelOne added cryptojacking detection and prevention into its cybersecurity offering. |
| AVG Technologies | AVG Technologies added real-time cryptojacking protection to its antivirus products to help safeguard users against its covert cryptocurrency mining attacks. |
| LogPoint | T o address the threat of cryptojacking, LogPoint added new capabilities to its cybersecurity platform designed to guard enterprise networks against unauthorized mining. |
| ACTE | To create awareness around Cryptojacking, ACTE started learning programs and training sessions for organizations to learn how to tackle this latest-cyber threat. |
By 2024 and early 2025, the industry for cybersecurity was reacting to the explosive threat of cryptojacking, enhancing current solutions and adding capabilities that could identify and block rogue cryptocurrency projects. The fact that premium solutions by companies such as SentinelOne, AVG Technologies and LogPoint have added advanced cryptojacking detection only polishes its image measures against the stealthy threat.
In addition, organizations like ACTE have laid stress upon education and awareness, initiating programs to educate and arm firms against prospective cryptojacking attacks. This reflects a unified industry initiative to address the increasing menace of cryptojacking, ensuring effective defense against such attacks for individual users as well as organizations.
In 2020 to 2024, the industry witnessed high growth rates, owing to the increase in unauthorized cryptocurrency mining attacks. The attackers used hacked accounts to mine digital currencies illicitly on cloud accounts, enterprise networks and endpoint devices, raising costs and degrading performance.
Firms place endpoint security solutions, cloud threat detection, and anomaly detection based on AI at the forefront of their agendas to address threats. Governments also enact more robust cybersecurity guidelines, which pushed companies to deploy compliance-based security models.
The industry will likely change from 2025 to 2035 by adding AI-driven autonomous security platforms capable of detecting and neutralizing threats in real-time. Quantum-proof encryption techniques will be developed to thwart sophisticated cryptojacking attempts, and blockchain-based security paradigms will enable decentralized sharing of threat intelligence.
Zero-trust security frameworks will be embraced by organizations to block unauthorized access and reduce attack surfaces. There will also be the development of sustainable cybersecurity technologies to lower the energy cost of cryptojacking monitoring and mitigation.
Comparative Market Shift Analysis (2020 to 2024 vs. 2025 to 2035)
| 2020 to 2024 | 2025 to 2035 |
|---|---|
| Increasing awareness led to the initial enterprise adoption of cryptojacking detection solutions. | Extensive use of AI-based solutions for threat hunting and automated response systems. |
| Adoption of cybersecurity frameworks that mandate detection and prevention controls. | Implementation of tighter compliance requirements and global cybersecurity partnerships that enhance cross-border threat intelligence exchange. |
| Adoption of signature-based detection and anomaly monitoring controls. | Transition to AI/ML algorithms for real-time detection and automated response in cloud, IoT, and edge environments. |
| Early-stage automation for alerting and blocking malicious activity. | Automated security processes with full integration of predictive analytics to block cryptojacking attempts. |
| Stand-alone solutions with minimal integration into broader cybersecurity ecosystems. | Seamless integration with Security Information and Event Management (SIEM), Extended Detection and Response (XDR), and Zero Trust frameworks. |
The industry is expanding as businesses seek robust protection against unauthorized cryptocurrency mining. However, evolving cyber threats escalate the challenge. Hackers continually improve cryptojacking techniques, thus, making it problematic for security solutions to remain ahead. AI-driven threat detection and frequent system updates are the requirements for companies to counteract the emerging risks.
The rise of cloud computing facilitates new attack surfaces through which hackers can utilize the cloud resources for cryptojacking. Companies in the business of cloud face a threat of higher operational expense costs of the misappropriation of resources. Application of the security framework at multiple levels, constant analysis, and incorporation of anomaly detection tools are the successful remedy for the aforementioned money and process risks.
A lack of education and the fact that small and medium-sized enterprises (SMEs) do not have sufficient cybersecurity infrastructures are the key factors for limiting industry penetration. Many organizations are not aware of the potential danger of cryptojacking leading to the problems of low provisioning security solutions.
The use of awareness campaigns, the offering of low-cost alternatives, and the capitalization on cybersecurity by training schemes will be the main drivers in the increase of industry uptake and the promotion of resilience.
The cyber security industry`s technological evolution and wide spread of competition claim for the companies to be up to date with innovations. Big cybersecurity corporations and new companies, which are just starting, push the tech to make quantum leaps.
In order to cope with the said risks, companies need to prioritize the development of complex detection for cryptojacking, easy integration with existing solutions, and proactive intelligence about the threats.
| Countries | CAGR (2025 to 2035) |
|---|---|
| USA | 15.1% |
| UK | 16.4% |
| France | 14.9% |
| Germany | 14.7% |
| Italy | 13.8% |
| South Korea | 16.1% |
| Japan | 14.3% |
| China | 17.2% |
| Australia | 13.5% |
| New Zealand | 12.9% |
The USA has a significant share in the industry due to its advanced cybersecurity infrastructure, regulation environment, and wide use of the cloud. With growing cyber-attacks on federal agencies and corporations, AI-driven threat intelligence, endpoint security, and blockchain security solution expenditure is escalating.
Strict cybersecurity policies and programs of the USA government, including national defense programs against cyberattacks, are boosting the industry. The rising adoption of IoT and smart home appliances also calls for advanced security solutions, and hence, the USA is one of the major industries.
The UK industry is rising at an impressive rate due to the evolution in fintech, online banking, and e-commerce websites, which are all legitimate targets for cryptojacking attacks. The country's regulatory bodies are tightening cybersecurity measures, and organizations are having to invest in robust security mechanisms.
The international trend towards cloud computing and remote work patterns in the post-pandemic scenario has left companies vulnerable to more malicious crypto-mining threats. The emphasis in the UK on developing cybersecurity innovation and AI-based security solutions is also driving industry uptake.
The development of France's industry is driven by the increasing adoption of smart infrastructure and data centers. Increased use of the cloud in sectors such as healthcare, finance, and government services has triggered a boom in cryptojacking in France.
The government's push towards digitalization and enhanced security measures is also propelling the industry's development. Furthermore, collaborations between private and public sectors in new AI-based threat detection technologies are driving France's dominance of the industry.
As a result of Germany's dominance in industry automation and IoT, the country is a high-value target industry for cryptojacking solutions. Germany's industrialized manufacturing sector and automotive industries are network-dependent infrastructures, making them more vulnerable to cryptojacking attacks.
German firms are making investments in cyber expenditure, increasingly endpoint security and blockchain-influenced threat protection. State-funded cyber security initiatives and compliance obligations are additionally compelling the industry to push broad acceptance of cryptojacking remedies.
Italy's crypto jacking solution industry is following a steady growth trend with the rising reliance on cloud services and finance cyber security solutions. The country's banking and finance industry has been amongst the key areas of interest for crypto jacking assaults, causing rising security expenditures.
The government is also actively promoting digital security consciousness and implementing stringent data protection laws. Moreover, the increasing usage of AI-based security solutions by Italian companies is contributing further to the growth of the industry.
The prevalence of South Korea in the crypto space provides a significant risk zone for crypto jacking. South Korea's high-tech infrastructure, paired with the rapid evolution of 5G and IoT, has kept the vulnerabilities open to illicit mining.
The government of South Korea is also accelerating the process towards curbing crypto-related cybercrimes, thereby compelling the investment in crypto jacking prevention software. In addition, local cybersecurity firms are leveraging AI and blockchain to expand detection capabilities, putting South Korea at the forefront of the world industry.
Japan's industry is growing, owing to digitalization is spreading rapidly in sectors such as finance, e-commerce, and healthcare. The nation's widespread adoption of digital payments and cloud computing makes it a prime target for cryptojacking threats.
The government's aggressive stand on cybersecurity, including the imposition of national security standards, is compelling businesses to adopt advanced security measures. The country's head start in AI and robotics is also aiding the development of more sophisticated cryptojacking detection tools.
China's industry prospers amidst strict cryptocurrency regulations. The country's pervasive digital footprint and enormous IoT, smart city, and AI-enabled application adoption left it vulnerable to cryptojacking. Despite regulation of numerous crypto trading and mining activities, cybercriminals continue to leverage digital environments for illicit mining. The government's emphasis on cyber protection and the potential of AI and machine learning for threat analysis is propelling the industry.
The Australian industry is expanding due to a rise in government-initiated cybersecurity initiatives and heightened cloud dependence. The financial sector and small and medium-sized enterprises are under threat from expanding cryptojacking, which is prompting organizations to invest in security products that use AI.
Additionally, Australia's digitalization strategies and adoption of cybersecurity standards of compliance are creating opportunities for security vendors to offer innovative cryptojacking mitigation solutions.
The New Zealand digital economy is growing aggressively, thus creating increasing demand for cryptojacking products. Expansion in cloud computing, online banking, and remote work has created new security vulnerabilities. The government is taking the implementation of data protection regulations and cybersecurity awareness initiatives seriously to address the cryptojacking attack.
Apart from this, collaboration among regional cybersecurity providers and international security players is fuelling the aggressive development of cutting-edge cryptojacking detection and blocking products.
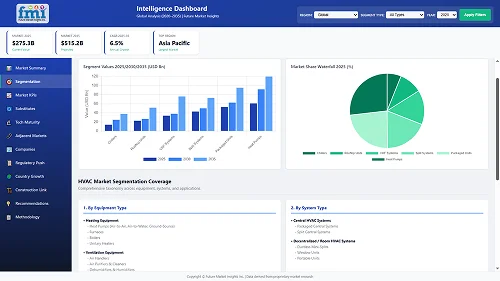
Anti-cryptojacking Solution Segment holds Dominating Market Share in the Industry.
| Component | Share (2025) |
|---|---|
| Anti-cryptojacking Solution | 20.7% |
The anti-cryptojacking solution segment is anticipated to hold 20.7% of the total industry share by 2025. Such tools fall in the category of browser-based security solutions, endpoint protection software, and network-based detection systems that can monitor and block cryptojacking attempts.
To combat the rapidly evolving nature of mining malware, Dell, Cisco Umbrella, McAfee Endpoint Security, and Palo Alto Networks are some of the advanced security providers that are improving their cloud-based threat intelligence platform. To that end, AI-powered detectors are being incorporated into procedures to enable real-time threat monitoring and automated response measures.
Moreover, many browser add-ons, like No Coin and Miner Block, find use in blocks running crypto-jacking (groups that run scripts on websites for unauthorized CPU use), and Microsoft Defender for Endpoint provides corporation-grade security solutions for enterprises and organizations to lessen unauthorized mining bills.
Managed security services (MSS), incident response, and threat intelligence solutions make up 18.3% of the industry share in the Services segment. As cryptojacking attacks span cloud, hybrid, and on-premise environments, many businesses are turning to third-party service providers for cyber security management.
Key cybersecurity firms, such as IBM X-Force Threat Intelligence, FireEye Managed Defense, and Crowd Strike Falcon Complete, offer real-time monitoring and forensic analysis to keep businesses ahead of cryptojacking attacks. These services offer great value for enterprises where in-house security expertise is not available, and a constant shield against ever-evolving threats is necessary.
Moreover, mandatory regulatory compliance like GDPR and CCPA is driving organizations towards more proactive threat monitoring, etc., and Encrypting data. North America & Europe dominate the cryptojacking prevention industry, while Asia-Pacific is experiencing rapid adoption of managed security services owing to increased penetration of Cloud infrastructure.
| Deployment Mode | CAGR (2025 to 2035) |
|---|---|
| Cloud-b ased | 17.1% |
The cloud-based segment is anticipated to grow rapidly, at a 17.1% CAGR from 2025 to 2035. Additionally, the growing adoption of cloud services by enterprises, along with the need for scalable AI-driven security solutions, are expected to fuel the growth of the cloud-based segment of the cryptojacking prevention tools industry.
As businesses migrate workloads to AWS, Microsoft Azure, and Google Cloud, they need real-time monitoring and automated threat detection to stop cryptojacking attacks targeting virtual machines and cloud-native environments. Major cybersecurity companies like Palo Alto Networks, Trend Micro, and Crowd Strike have introduced AI-enhanced cloud security platforms that use real-time detection to stop mining malware.
In addition, cloud-based deployment decreases dependency on on-premises hardware, which enables it to reduce operational costs and improve incident response capability. Cloud-based anti-crypto jacking solutions are likely to take the lead owing to the increase in enterprise cloud security spending, which is expected to combat by 20% as time advances in the year 2025.
Due to data sensitivity and heavy regulations on their operations, On-Premises, the segment will register approximately 12.8% CAGR during the forecast years. On-premise cryptojacking is preferred by sectors like government, banking, healthcare, and defense, which require a direct grip over the security infrastructure and data privacy.
Organizations handling highly sensitive information usually use firewall-based anti-crypto jacking tools and endpoint detection and response (EDR) systems to protect their internal networks. Symantec, Fortinet, and Checkpoint provide similar on-premise solutions for enterprises wanting high-performance detection without external dependency.
Competition in the industry is intense, with cybersecurity giants and specialized threat intelligence companies seeking answers to the unauthorized cryptocurrency mining challenge. Cybercriminals use an entire gamut of sophisticated attack mechanisms-from browser mining scripts to file less malware-and hence organizations look for AI-based, behavior-based, real-time threat detection solutions to protect their IT infrastructure.
In the hands of market leaders such as Cisco Systems, IBM Corporation, Palo Alto Networks, Symantec (Broadcom Inc.), and McAfee (Trellix), the integration of cryptojacking prevention into their wider endpoint protection, network security, and cloud security solutions works in their favor.
These large organizations use machine learning-based anomaly detection, heuristic analysis, and real-time threat intelligence to counter the exploitation of computing resources for any illicit activities.
The competitive scenario also includes newcomers and more specialized cyber guys focused on generic cryptojacking prevention mechanisms, blockchain-based security frameworks, and SOC (Security Operations Center) integration.
Their acquisition strategies and partnerships with cloud service providers, financial institutions, and government agencies will also redefine the industry dynamics as far as enterprises urge proactive defense against emerging cryptojacking tactics.
With the increasing regulatory scrutiny of crypto-related cyber threats, organizations are now looking for zero-trust architecture, automated remediation capabilities, and endpoint resilience frameworks. Companies that can combine deep threat intelligence with multi-layered protection reach the top of the companies working in this high-profile cybersecurity region.
Market Share Analysis by Company
| Company Name | Estimated Market Share (%) |
|---|---|
| Cisco Systems | 20-25% |
| IBM Corporation | 15-20% |
| Palo Alto Networks | 12-17% |
| Symantec (Broadcom Inc.) | 10-15% |
| McAfee (Trellix) | 8-12% |
| Other Companies (combined) | 30-40% |
| Company Name | Key Offerings/Activities |
|---|---|
| Cisco Systems | Provides network-level cryptojacking detection via its Talos Intelligence platform. |
| IBM Corporation | Integrates cryptojacking detection with its broader Security Operations Center (SOC) solutions. |
| Palo Alto Networks | Delivers endpoint protection through Cortex XDR, enhancing visibility and automating response against cryptojacking attacks. |
| Symantec (Broadcom Inc.) | Provides multi-layered defenses with cloud analytics and automated threat intelligence to counter crypto-mining malware. |
| McAfee (Trellix) | Focuses on endpoint and cloud security, using real-time threat intelligence to detect abnormal CPU usage linked to cryptojacking. |
Key Company Insights
Cisco Systems (20-25%)
Cisco leads the industry by leveraging its extensive network infrastructure expertise. The company integrates cryptojacking detection into its broader security portfolio, using its Talos Intelligence platform to provide real-time insights into emerging threats.
IBM Corporation (15-20%)
IBM focuses on integrating cryptojacking detection into its security intelligence platform, QRadar. The solution uses AI and machine learning to identify abnormal network behaviors and flag unauthorized cryptocurrency mining activities.
Palo Alto Networks (12-17%)
Palo Alto Networks addresses cryptojacking through its Cortex XDR platform, combining endpoint protection, threat intelligence, and behavioral analytics. The company focuses on automating threat detection and response to reduce the attack surface.
Symantec (Broadcom Inc.) (10-15%)
Symantec offers multi-layered protection against cryptojacking by using advanced machine learning algorithms to detect malicious mining scripts across endpoints, networks, and cloud environments.
McAfee (Trellix) (8-12%)
McAfee focuses on delivering endpoint security solutions capable of detecting abnormal CPU usage and preventing unauthorized crypto-mining activities. Its cloud-native solutions leverage global threat intelligence to provide real-time monitoring and automated incident response.
Other Key Players (30-40% Combined)
By component, the segment is categorized into anti-cryptojacking solution, services (professional services, consulting, training and education, support and maintenance), and managed services.
By deployment mode, the segment is classified into cloud-based and on-premises.
By industry, the segment is categorized into BFSI, retail, government and public sector, manufacturing, healthcare, education, energy and utilities, and others.
Key countries of North America, Latin America, Western Europe, Eastern Europe, East Asia, South Asia & pacific, Middle East and Africa (MEA) have been covered in the report.
The industry is expected to reach USD 22.1 billion in 2025.
The industry is projected to grow to USD 100.3 billion by 2035.
The industry is expected to grow at a CAGR of 16.3% from 2025 to 2035.
China is expected to grow at the fastest rate, with a CAGR of 17.2% during the forecast period.
The anti-cryptojacking solution segment is among the most widely used in the industry.
Cisco Systems, IBM Corporation, Palo Alto Networks, Symantec (Broadcom Inc.), McAfee (Trellix), Trend Micro, CyberArk, Okta, Fortinet, Zscaler, and Accops are the key players in the industry.
Full Research Suite comprises of:
Market outlook & trends analysis
Interviews & case studies
Strategic recommendations
Vendor profiles & capabilities analysis
5-year forecasts
8 regions and 60+ country-level data splits
Market segment data splits
12 months of continuous data updates
DELIVERED AS:
PDF EXCEL ONLINE
Solution Styrene Butadiene Rubber (S-SBR) Market Size and Share Forecast Outlook 2025 to 2035
NGS Solution for Early Cancer Screening Market Size and Share Forecast Outlook 2025 to 2035
5PL Solutions Market
High-Resolution Anoscopy Market Size and Share Forecast Outlook 2025 to 2035
mHealth Solutions Market Size and Share Forecast Outlook 2025 to 2035
Super Resolution Microscope Market Insights - Size, Share & Forecast 2025 to 2035
G-3 PLC Solution Market – Smart Grids & Connectivity
Docketing Solution Market Size and Share Forecast Outlook 2025 to 2035
Long Haul Solutions Market Size and Share Forecast Outlook 2025 to 2035
eClinical Solutions and Software Market Insights - Trends & Forecast 2025 to 2035
E-tailing Solutions Market Growth – Trends & Forecast 2020-2030
Connected Solutions for Oil & Gas Market Insights – Trends & Forecast 2020-2030
Biocontrol Solutions Market Size and Share Forecast Outlook 2025 to 2035
WealthTech Solutions Market Size and Share Forecast Outlook 2025 to 2035
Smart Home Solutions Market Size and Share Forecast Outlook 2025 to 2035
Geospatial Solution Market Analysis - Size, Share, and Forecast Outlook for 2025 to 2035
E-Learning Solution Market by Solution, Deployment, & Region Forecast till 2035
eDiscovery solution Market
Intravenous Solution Compounders Market Size and Share Forecast Outlook 2025 to 2035
Control Room Solution Market Size and Share Forecast Outlook 2025 to 2035
Thank you!
You will receive an email from our Business Development Manager. Please be sure to check your SPAM/JUNK folder too.
Chat With
MaRIA