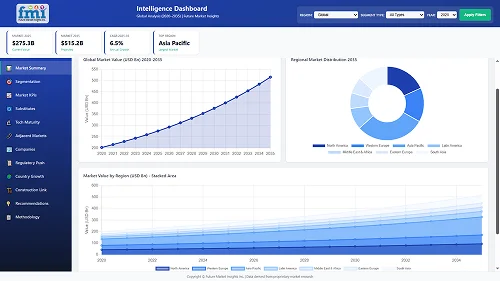
[272 Pages Report] The global embedded security for internet of things held USD 2,525 Million in 2017 and is projected to secure almost USD 11,125 Million by the end of 2027.
| Attribute | Details |
|---|---|
| Estimated market size of global embedded security for IoT in 2017 | USD 2,525 Million |
| Projected market size of global embedded security for IoT by 2027 | USD 11,125 Million |
| CAGR during 2017 to 2027 | 15.9% |
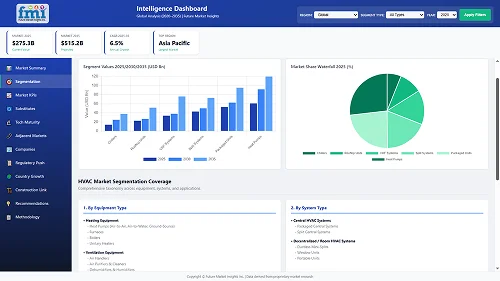
The controller chip sector of the global embedded security for Internet of Things (IoT) market is expected to increase at a CAGR of 14.7% between 2017 and 2027.
In 2017, the controller chip category is expected to be worth USD 2,300 Million accounting for more than 80% of global market revenue.
The controller chip segment is predicted to stay dominating during the forecast period. Between 2017 and 2027, it is expected to generate about USD 6,800 Million in additional revenue.
Due to increasing intensity of cyber-attacks, various associations that promote best practices for implementing IoT solutions have issued guidelines for implementation and adoption of necessary security solutions in order to protect against such attacks. Implementation of embedded controller chipsets is one such guideline promoting the adoption of embedded solutions for IoT.
An increasing use of controller chipsets in order to ensure protection from cyber-attacks is expected to drive revenue growth of the controller chip segment in the global embedded security for Internet of Things (IoT) market.
For instance, in December 2016, a non-profit multi-industry association called Smart Card Alliance promoting best practices for smart card applications in the U.S. and Latin America issued guidelines for the adoption of embedded hardware security (controller chipset) solutions involving end devices to include hardware features and functions to ensure that the required security standards are implemented and maintained.
Increasing adoption of IoT globally is resulting in a large number of devices being connected, communicating and exchanging data with each other seamlessly. Devices connected through IoT networks are used in verticals including smart cities, healthcare, industrial automation, retail, agriculture and others. According to U.S. based IoT solutions provider Cisco Systems Inc., around 7% of global mobile data traffic will come from devices connected through the IoT by 2020.
A rising number of IoT enabled connected devices will result in increased demand for security solutions in terms of hardware. Increasing focus on the component aspect of security is the new trend in the global market that is likely to fuel the growth of the controller chip segment.
Security software alone is not sufficient to protect IoT devices against cyber-attacks and malware and needs to be supported by reliable hardware for data processing and safe storage. Vulnerable hardware components are susceptible to unauthorised access and data theft, thereby compromising the security of the overall system, which is why OEMs are turning towards embedded component suppliers who can address these security issues effectively.
In January 2015, Canadian telecom solutions provider BlackBerry launched a cloud-based IoT platform with device management features enabling data gathering from a range of devices and networks.
The platform enables application developers, business partners, and others to collaborate on different aspects of IoT solutions including security. Initially, the platform was targeted at the automotive and shipping sector and in future, it will be extended to other verticals such as energy and healthcare.
Although a number of governing authorities have issued guidelines to be followed by IoT device manufacturers so as to protect against cyber-attacks happening on IoT networks and devices, many device manufacturers and users do not strictly adhere to these guidelines nor take any precautionary measures. Non-adherence to security guidelines results in security lapses, which cyber attackers take advantage of, resulting in unauthorised data access and data thefts.
This is a major factor hampering revenue growth of the global embedded security for Internet of Things (IoT) market.
Global embedded security for internet of things (IoT) market was estimated to account for USD 2,525 Million in 2017 and is expected to grow at a CAGR of 15.9% by 2027.
Cisco Systems, Inc., Infineon Technologies AG, NXP Semiconductors N.V., and Samsung Electronics Co., Ltd. are some prominent embedded security for IoT service providers
Table 1: North America Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Component, 2017–2027
Table 2: North America Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Application, 2017–2027
Table 3: North America Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Vertical, 2017–2027
Table 4: Latin America Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Component, 2017–2027
Table 5: Latin America Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Application, 2017–2027
Table 6: Latin America Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Vertical, 2017–2027
Table 7: APEJ Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Component, 2017–2027
Table 8: APEJ Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Application, 2017–2027
Table 9: APEJ Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Vertical, 2017–2027
Table 10: Japan Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Component, 2017–2027
Table 11: Japan Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Application, 2017–2027
Table 12: Japan Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Vertical, 2017–2027
Table 13: Eastern Europe Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Component, 2017–2027
Table 14: Eastern Europe Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Application, 2017–2027
Table 15: Eastern Europe Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Vertical, 2017–2027
Table 16: Western Europe Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Component, 2017–2027
Table 17: Western Europe Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Application, 2017–2027
Table 18: Western Europe Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Vertical, 2017–2027
Table 19: MEA Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Component, 2017–2027
Table 20: MEA Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Application, 2017–2027
Table 21: MEA Embedded Security for Internet of Things Market Value (US$ Mn) Forecast, By Vertical, 2017–2027
Figure 1: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 2: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 3: Global Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Component, 2017–2027
Figure 4: Global Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Component, 2017–2027
Figure 5: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Software Segment, 2017–2027
Figure 6: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Software Segment, 2017–2027
Figure 7: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Controller Chip Segment, 2017–2027
Figure 8: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Controller Chip Segment, 2017–2027
Figure 9: Global Embedded Security for Internet of Things Market Attractiveness Index, By Component, 2017–2027
Figure 10: Global Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Application, 2017–2027
Figure 11: Global Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Application, 2017–2027
Figure 12: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Smart Factory Segment, 2017–2027
Figure 13: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Smart Factory Segment, 2017–2027
Figure 14: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Smart Grid Segment, 2017–2027
Figure 15: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Smart Grid Segment, 2017–2027
Figure 16: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Connected Car Segment, 2017–2027
Figure 17: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Connected Car Segment, 2017–2027
Figure 18: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Networking Equipment Segment, 2017–2027
Figure 19: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Networking Equipment Segment, 2017–2027
Figure 20: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Computing Devices Segment, 2017–2027
Figure 21: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Computing Devices Segment, 2017–2027
Figure 22: Global Embedded Security for Internet of Things Market Attractiveness Index, By Application, 2017–2027
Figure 23: Global Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Vertical, 2017–2027
Figure 24: Global Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Vertical, 2017–2027
Figure 25: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Retail Segment, 2017–2027
Figure 26: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Retail Segment, 2017–2027
Figure 27: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Aerospace and defense Segment, 2017–2027
Figure 28: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Aerospace and defense Segment, 2017–2027
Figure 29: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Healthcare Segment, 2017–2027
Figure 30: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Healthcare Segment, 2017–2027
Figure 31: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Gaming Segment, 2017–2027
Figure 32: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Gaming Segment, 2017–2027
Figure 33: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Automotive Segment, 2017–2027
Figure 34: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Automotive Segment, 2017–2027
Figure 35: Global Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), by Others Segment, 2017–2027
Figure 36: Global Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), by Others Segment, 2017–2027
Figure 37: Global Embedded Security for Internet of Things Market Attractiveness Index, By Vertical, 2017–2027
Figure 38: Global Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Region, 2017–2027
Figure 39: Global Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Region, 2017–2027
Figure 40: North America Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 41: North America Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 42: Latin America Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 43: Latin America Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 44: Asia Pacific excluding Japan Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 45: Asia Pacific excluding Japan Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 46: Japan Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 47: Japan Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 48: Western Europe Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 49: Western Europe Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 50: Eastern Europe Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 51: Eastern Europe Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 52: Middle East & Africa Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 53: Middle East & Africa Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 54: Global Embedded Security for Internet of Things Market Attractiveness Index, By Vertical, 2017–2027
Figure 55: North America Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Country, 2017 & 2027
Figure 56: North America Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Country, 2017–2027
Figure 57: U.S. Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 58: U.S. Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 59: Canada Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 60: Canada Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 61: North America Embedded Security for Internet of Things Market Attractiveness Analysis, By Component, 2017–2027
Figure 62: North America Embedded Security for Internet of Things Market Attractiveness Analysis, By Application, 2017–2027
Figure 63: North America Embedded Security for Internet of Things Market Attractiveness Analysis, By Vertical, 2017–2027
Figure 64: North America Embedded Security for Internet of Things Market Attractiveness Analysis, By Region, 2017–2027
Figure 65: North America Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017 & 2027
Figure 66: Latin America Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Country, 2017 & 2027
Figure 67: Latin America Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Country, 2017–2027
Figure 68: Brazil Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 69: Brazil Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 70: Mexico Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 71: Mexico Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 72: Argentina Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 73: Argentina Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 74: Rest of Latin America Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 75: Rest of Latin America Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 76: Latin America Embedded Security for Internet of Things Market Attractiveness Analysis, By Component, 2017–2027
Figure 77: Latin America Embedded Security for Internet of Things Market Attractiveness Analysis, By Application, 2017–2027
Figure 78: Latin America Embedded Security for Internet of Things Market Attractiveness Analysis, By Vertical, 2017–2027
Figure 79: Latin America Embedded Security for Internet of Things Market Attractiveness Analysis, By Region, 2017–2027
Figure 80: Latin America Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017 & 2027
Figure 81: APEJ Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Country, 2017 & 2027
Figure 82: APEJ Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Country, 2017–2027
Figure 83: China Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 84: China Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 85: India Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 86: India Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 87: ASEAN Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 88: ASEAN Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 89: Australia and New Zealand Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 90: Australia and New Zealand Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 91: Rest of APEJ Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 92: Rest of APEJ Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 93: APEJ Embedded Security for Internet of Things Market Attractiveness Analysis, By Component, 2017–2027
Figure 94: APEJ Embedded Security for Internet of Things Market Attractiveness Analysis, By Application, 2017–2027
Figure 95: APEJ Embedded Security for Internet of Things Market Attractiveness Analysis, By Vertical, 2017–2027
Figure 96: APEJ Embedded Security for Internet of Things Market Attractiveness Analysis, By Region, 2017–2027
Figure 97: APEJ Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017 & 2027
Figure 98: Japan Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 99: Japan Embedded Security for Internet of Things Market Absolute $ Opportunity (US$ Mn), 2017–2027
Figure 100: Japan Embedded Security for Internet of Things Market Attractiveness Analysis, By Component, 2017–2027
Figure 101: Japan Embedded Security for Internet of Things Market Attractiveness Analysis, By Application, 2017–2027
Figure 102: Japan Embedded Security for Internet of Things Market Attractiveness Analysis, By Vertical, 2017–2027
Figure 103: Japan Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017 & 2027
Figure 104: Eastern Europe Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Country, 2017 & 2027
Figure 105: Eastern Europe Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Country, 2017–2027
Figure 106: Russia Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 107: Russia Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 108: Poland Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 109: Poland Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 110: Rest of Eastern Europe Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 111: Rest of Eastern Europe Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 112: Eastern Europe Embedded Security for Internet of Things Market Attractiveness Analysis, By Component, 2017–2027
Figure 113: Eastern Europe Embedded Security for Internet of Things Market Attractiveness Analysis, By Application, 2017–2027
Figure 114: Eastern Europe Embedded Security for Internet of Things Market Attractiveness Analysis, By Vertical, 2017–2027
Figure 115: APEJ Embedded Security for Internet of Things Market Attractiveness Analysis, By Country, 2017–2027
Figure 116: Eastern Europe Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017 & 2027
Figure 117: Western Europe Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Country, 2017 & 2027
Figure 118: Western Europe Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Country, 2017–2027
Figure 119: Germany Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 120: Germany Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 121: France Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 122: France Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 123: U.K. Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 124: U.K. Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 125: Spain Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 126: Spain Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 127: Italy Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 128: Italy Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 129: Nordic Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 130: Nordic Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 131: Benelux Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 132: Benelux Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 133: Rest of Western Europe Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 134: Rest of Western Europe Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 135: Western Europe Embedded Security for Internet of Things Market Attractiveness Analysis, By Component, 2017–2027
Figure 136: Western Europe Embedded Security for Internet of Things Market Attractiveness Analysis, By Application, 2017–2027
Figure 137: Western Europe Embedded Security for Internet of Things Market Attractiveness Analysis, By Vertical, 2017–2027
Figure 138: Western Europe Embedded Security for Internet of Things Market Attractiveness Analysis, By Region, 2017–2027
Figure 139: Western Europe Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017 & 2027
Figure 140: MEA Embedded Security for Internet of Things Market Value (%) & BPS Analysis, By Country, 2017 & 2027
Figure 141: MEA Embedded Security for Internet of Things Market Revenue Y-o-Y Growth, By Country, 2017–2027
Figure 142: GCC Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 143: GCC Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 144: North Africa Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 145: North Africa Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 146: South Africa Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 147: South Africa Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 148: Rest of MEA Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017–2027
Figure 149: South Africa Embedded Security for Internet of Things Market Absolute $ Opportunity, 2017–2027
Figure 150: MEA Embedded Security for Internet of Things Market Attractiveness Analysis, By Component, 2017–2027
Figure 151: MEA Embedded Security for Internet of Things Market Attractiveness Analysis, By Application, 2017–2027
Figure 152: MEA Embedded Security for Internet of Things Market Attractiveness Analysis, By Vertical, 2017–2027
Figure 153: MEA Embedded Security for Internet of Things Market Attractiveness Analysis, By Region, 2017–2027
Figure 154: MEA Embedded Security for Internet of Things Market Value (US$ Mn) & Y-o-Y Growth (%), 2017 & 2027
Full Research Suite comprises of:
Market outlook & trends analysis
Interviews & case studies
Strategic recommendations
Vendor profiles & capabilities analysis
5-year forecasts
8 regions and 60+ country-level data splits
Market segment data splits
12 months of continuous data updates
DELIVERED AS:
PDF EXCEL ONLINE
Embedded Lending Market Size and Share Forecast Outlook 2025 to 2035
Embedded AI Market Size and Share Forecast Outlook 2025 to 2035
Embedded Universal Integrated Circuit Card (eUICC) Market Size and Share Forecast Outlook 2025 to 2035
Embedded Finance Market Size and Share Forecast Outlook 2025 to 2035
Embedded Controllers Market Size and Share Forecast Outlook 2025 to 2035
Embedded Multimedia Card Market Size and Share Forecast Outlook 2025 to 2035
Embedded Hypervisor Market Report – Trends, Demand & Industry Forecast 2025–2035
Smart Embedded Systems – AI-Optimized for IoT & 5G
Embedded Banking Market Insights – Growth & Forecast 2024-2034
Embedded Intelligence Market Growth – Trends & Industry Forecast 2023-2033
Embedded Business Intelligence Market Growth – Trends & Forecast 2023-2033
Embedded Smart Cameras Market Growth – Trends & Forecast 2023-2033
Device-Embedded Biometric Authentication Market Size and Share Forecast Outlook 2025 to 2035
Europe Embedded Finance Market – Trends & Forecast 2025 to 2035
Europe Embedded Banking Market - Trends & Forecast 2025 to 2035
Military Embedded Systems Market Size and Share Forecast Outlook 2025 to 2035
Low-Code Embedded Analytics Market Growth - Trends & Forecast 2025 to 2035
Industrial Embedded Systems Market Size and Share Forecast Outlook 2025 to 2035
Automotive Embedded System Market Growth - Trends & Forecast 2024 to 2034
Security Alarm Communicator Market Size and Share Forecast Outlook 2025 to 2035
Thank you!
You will receive an email from our Business Development Manager. Please be sure to check your SPAM/JUNK folder too.
Chat With
MaRIA